This archives have been downloaded from geocities.com/mybabywhy/rk.tar.gz
[kmaster@christophe sotm29]$ md5sum rk.tar.gz b308d1ed5b63aa0f0ef88d395388d331 rk.tar.gz [kmaster@christophe sotm29]$ tar tvzf rk.tar.gz drwxr-xr-x 1000/1000 0 2002-09-04 09:17:45 sand/ -rw------- root/root 539 2002-05-25 02:36:59 sand/h -rwx------ root/root 98 2002-03-18 13:21:58 sand/logclear -rw------- root/root 512 2002-05-25 02:36:59 sand/hhh -rwxr-xr-x root/root 11906 2002-05-25 02:47:42 sand/ava -rwxr-xr-x root/root 4060 1983-09-26 01:45:00 sand/sense -rwx------ root/root 8268 1983-09-26 01:45:00 sand/sl2 -rwxr-xr-x informat/root 32756 2001-12-14 00:43:38 sand/ps -rwx--x--x root/root 4905 2003-05-17 04:43:39 sand/install -rwxr-xr-x informat/root 30640 2001-12-14 00:43:38 sand/netstat -rwx--x--x root/root 5468 2002-02-12 09:21:19 sand/sysinfo -rw-r--r-- root/root 692 2003-05-17 04:44:02 sand/hh -rwxr-xr-x informat/root 22328 2001-12-14 00:43:38 sand/ifconfig -rwxr-xr-x informat/root 48856 1983-09-26 01:45:00 sand/top -rwxr-xr-x root/root 134 2002-09-04 09:18:19 sand/.ttyoa -rw-r--r-- root/root 3725 2002-02-12 09:22:55 sand/chattr.tgz -rw-r--r-- root/root 79279 2002-02-12 09:23:03 sand/pico.tgz -rw-r--r-- root/root 59002 2002-02-12 09:23:10 sand/wget.tgz -rwxr-xr-x informat/root 36692 2001-12-14 00:43:38 sand/ls -rw-r--r-- root/root 2 2002-04-19 07:59:04 sand/libsss -rwxr-xr-x root/root 74 2002-03-18 16:18:19 sand/.ttyop -rwxr-xr-x root/root 59 2002-09-04 09:19:14 sand/.ttyof -rw-r--r-- root/root 5386 2002-04-19 08:11:41 sand/kde.c -rwxr-xr-x 1000/root 50 2002-05-25 02:35:45 sand/lpi -rwxr-xr-x root/root 13707 2002-07-11 05:13:06 sand/crontabs -rwx------ root/root 7165 1983-09-26 01:45:00 sand/swapd2 -rwxr-xr-x root/root 672527 2002-09-04 08:54:10 sand/ava1 -rwxr-xr-x root/root 672527 2002-07-31 15:03:22 sand/sshd
[kmaster@christophe sand]$ md5sum * 11f338eccae85db4dacea1005727249c ava 0c9fd2ff1740a4ae5b4a1a3a82846f44 ava1 1056897523b7b405d4a8fd7cea9d207b chattr.tgz f4198b40e62130ad6e173443037ded1b crontabs 5039776bb1a636b6a7ea2493d3a4d31c h 18d0615f33203484ec58eaf88a022ca5 hh 2255c96c5c35d2ec9796a12430d6d3a8 hhh bbdf9f3d6ed21c03b594adcd936c2961 ifconfig d8c4a5c773f4e72f6e9451c2b498b78e install 6a8c2e85a8c30a45890aabcc309a910f kde.c 3af0bf9dc137cb0122f491a03578fa8d libsss 49d1b847a9639501a001036454118a59 logclear 2b5a327879d5d8a0d98890591b613cb4 lpi 9e7165f965254830d0525fda3168fd7d ls c0e8b6ff00433730794eda274c56de3f netstat 9ede1ac808e3edea864aa13703bc39ad pico.tgz a71c756f78583895afe7e03336686f8b ps 464dc23cac477c43418eb8d3ef087065 sense 4cfae8c44a6d1ede669d41fc320c7325 sl2 11f1d47a7338438f235080b8e920088b sshd 6c0f96c1e43a23a21264f924ae732273 swapd2 cd49bf4fb07d350763fcece2d6b40793 sysinfo 58a7e5abe4b01923c619aca3431e13a8 top 12c658d6f9f864450c1f6b593f17d92c wget.tgz
| Virus | File |
|---|---|
| PERL_ROOTKIT.C | sand/sense |
| ELF_BLITZ | sand/sl2 |
| ELF_ROOTKIT.C2 | sand/swapd2 |
SSH PRIVATE KEY for root@lessons.menchey.com
killall -9 /usr/bin/"(swapd)" rm -rf /usr/bin/tcp.log touch /usr/bin/tcp.log "(swapd)" >tcp.log &
SSH seed
[kmaster@christophe sand]$ strings ava /lib/ld-linux.so.2 __gmon_start__ libc.so.6 system __deregister_frame_info _IO_stdin_used __libc_start_main __register_frame_info GLIBC_2.0 PTRh, mv h /usr/include/icekey.h mv hh /usr/include/iceconf.h mv hhh /usr/include/iceseed.h mv ava1 /usr/bin/"smbd -D" "smbd -D"
ava is an installer for the SSH server ava1 / smbd -D and its configuration file.
[kmaster@christophe sand]$ head sense #!/usr/bin/perl # Sorts the output from LinSniffer 0.03 [BETA] by Mike Edulla <medulla@infosoc.com>
[kmaster@christophe sand]$ strings sl2
...
[JSignal Caught. Exiting Cleanly.
[JSegmentation Violation Caught. Exiting Cleanly.
Unknown host %s
sendto
Usage: %s srcaddr dstaddr low high
If srcaddr is 0, random addresses will be used
socket
%i.%i.%i.%i
High port must be greater than Low port.
Using Google, these strings can be found in synk4.c, a Syn Flooder.
[kmaster@christophe sand]$ strings ps ... /dev/ttyop ... ps: unknown long option short form sort flag parse error unrecognized option or trailing garbage the name `%s' is not a tty ********* simple selection ********* ********* selection by list ********* -A all processes -C by command name -N negate selection -G by real group ID (supports names) -a all w/ tty except session leaders -U by real user ID (supports names) -d all except session leaders -g by session leader OR by group name -e all processes -p by process ID T all processes on this terminal -s processes in the sessions given a all w/ tty, including other users -t by tty g all, even group leaders! -u by effective user ID (supports names) r only running processes U processes for specified users x processes w/o controlling ttys t by tty ... %s/.psdevtab /tmp/psdevtab /etc/psdevtab ... /lib/modules/%s/psdatabase /boot/psdatabase /boot/psdatabase-%s /etc/psdatabase
There are unusual strings like /dev/ttyop or /tmp/psdevtab. It's a troyan version of ps.
#!/bin/bash # Made By ICE BLK='^[[1;30m' RED='^[[1;31m'
It's the trojan installer.
[kmaster@christophe sand]$ strings netstat ... Linux NET-3 Base Utilities Source: net-tools 1.32-alpha net-tools@lina.inka.de (Bernd Eckenfels) Kernelsource: 2.4.0-0.26 netstat 1.39 (2000-05-21) Fred Baumgarten, Alan Cox, Bernd Eckenfels, Phil Blundell, Tuan Hoang and others /dev/ttyoa ...
/dev/ttyoa is an unusual string for a netstat binary. It's a trojan.
#!/bin/bash
# Made By ICE
BLK='^[[1;30m'
...
#!bin/bash
unset HISTFILE
PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/usr/X11R6/bin:/root/bin:/usr/local/bin
echo "+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++"
echo "+++++ Informatziile pe care le-ai dorit boss:) +++++"
echo "+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++"
MYIPADDR=`/sbin/ifconfig eth0 | grep "inet addr:" | \
awk -F ' ' ' {print $2} ' | cut -c6-`
echo "Hostname : `hostname -f` ($MYIPADDR)"
echo "Alternative IP : `hostname -i`"
echo "Host : `hostname`"
...
Programm to collect information about the local machine.
[kmaster@christophe sand]$ head hh # This is ssh server systemwide configuration file. Port 2003 ListenAddress 0.0.0.0 HostKey /usr/include//icekey.h RandomSeed /usr/include//iceseed.h ServerKeyBits 768 LoginGraceTime 600 KeyRegenerationInterval 1 PermitRootLogin yes
[kmaster@christophe sotm29]$ md5sum sand/ifconfig bbdf9f3d6ed21c03b594adcd936c2961 sand/ifconfig
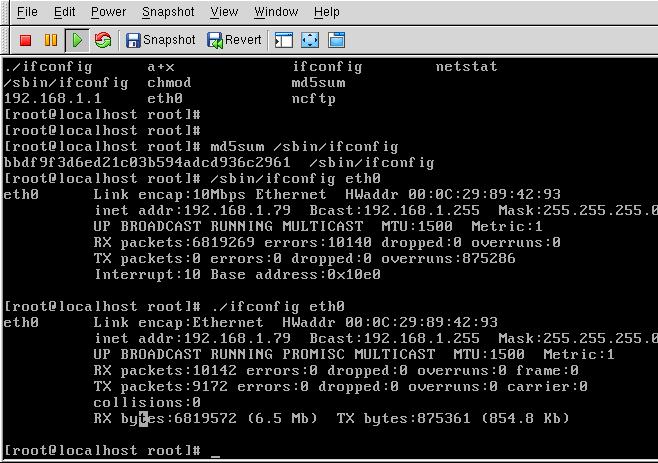
sand/ifconfig has been installed as /sbin/ifconfig
on the honeypot (MD5 checksum matches). This version of ifconfig hides
the promiscuous state of the interface eth0. An interface is usually
in promiscuous state when a sniffer is running and want to catch network
traffic directed to other hosts.
[kmaster@christophe sand]$ strings top|grep dev /dev %s/.psdevtab /tmp/psdevtab /etc/psdevtab /dev Cannot generate device number -> name mapping. /dev/ttyop
It uses psdevtab like ps trojan. It's a trojan version of the binary top.
[kmaster@christophe sand]$ cat .ttyoa 1 213.233 1 24.104 1 217.10 1 216 1 193 1 209.118 3 10001 3 10002 3 13064 3 19 3 69 3 6667 4 10001 4 6667 4 10002 4 19 4 69 4 13064
[kmaster@christophe sand]$ tar tvzf chattr.tgz -rwxr-xr-x IceNick/506 7512 2002-01-19 09:10:41 chattr
[kmaster@christophe sand]$ tar tvzf pico.tgz -rwxr-xr-x IceNick/506 165136 2002-01-19 09:11:01 pico
pico is a text editor. This version needs libncurses.so.4 so it don't work on RH 7.2 because this RH is shiped with version 5.
[kmaster@christophe sand]$ tar tvzf wget.tgz -rwxr-xr-x root/root 126024 2002-02-05 13:51:53 wget
These three archives can be used for missing binary needed by the trojan.
[kmaster@christophe sand]$ strings ls|grep dev /dev/ttyof
Trojan version of ls, it hides the files listed in /dev/ttyof.
[kmaster@christophe sand]$ cat libsss " [kmaster@christophe sand]$ grep libsss * install:mv libsss /usr/lib
?
[kmaster@christophe sand]$ cat .ttyop 3 swapd 3 psybnc 3 sl2 3 sl3 3 smbd 3 uptime 3 x2 3 startwu 3 scan 3 r00t
[kmaster@christophe sand]$ cat .ttyof psbnc smbd iceconf.h icekey.h icepid.h uptime startwu r00t
Read the source, Luck! Source file of a sniffer with
output file /usr/lib/libice.log.
[kmaster@christophe sand]$ cat lpi #!/bin/sh bb=`pwd` cd /usr/bin "(swapd)" & cd $bb
Shell script to run (swapd)
strings crontabs /lib/ld-linux.so.2 __gmon_start__ libc.so.6 __cxa_finalize system __deregister_frame_info _IO_stdin_used __libc_start_main __register_frame_info GLIBC_2.1.3 GLIBC_2.0 PTRh QVhx "smbd -D"
Binary that runs smbd -D.
[kmaster@christophe sand]$ strings swapd2 ... cant get SOCK_PACKET socket cant get flags cant set promiscuous mode ----- [CAPLEN Exceeded] ----- [Timed Out] ----- [RST] ----- [FIN] %s => %s [%d] eth0 tcp.log cant open log Exiting...
Binary version of the sniffer kde.c
[kmaster@christophe sand]$ strings ava1|grep SSH SSH-%d.%d-%.50s SSH-%d.%d-%[^ SSH_ORIGINAL_COMMAND SSH_CLIENT SSH_TTY SSH_AUTH_SOCK * Remote error: Invalid SSH_AGENT_SOCKET_DIR '%.100s', it should contain at least one /. SSH_AUTH_SOCK SSH PRIVATE KEY FILE FORMAT 1.1
SSH server
SSH server